With regard to web-based scenarios, there are five important application areas of data hiding ([1], [2, [3], [4] and [5]), which are shown in Fig. 2. The first two of them fall within the research interests of steganography and the rest are among the research topics of digital watermarking.
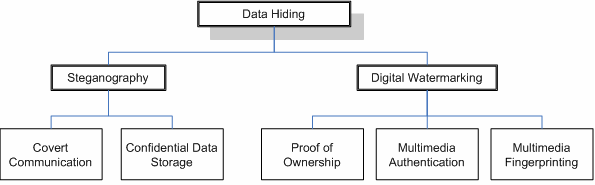
Fig. 2: Data hiding application areas
The first application area is called covert communication. It refers to the transmission of secret messages over the Internet (or other digital media). The purpose of covert communication is similar to the purpose of the transmission of encrypted data – it ensures the privacy of the communication between the involved parties. The additional advantage of covert communication is that by hiding the secret messages inside multimedia content, it hides the presence of the communication process itself. In this way, the fact that two parties communicate, should remain secret from any unauthorized third-parties.
The second application area concerns the invisible storage of confidential data [6]. The secure storage of sensitive private data such as credit card numbers, bank accounts, passwords, etc. can benefit from data hiding technologies. They are capable of making the encrypted private data invisible by hiding it inside multimedia, which enhances its protection and adds an additional security layer between the data and any potential hackers.
The third application area involves the protection of intellectual property rights and enables the proof of ownership. Data hiding technologies can embed information about the original author directly into the multimedia content. In this way, when arguments concerning the ownership of the multimedia arise, the legitimate author can prove its ownership claim.
The fourth application area – multimedia authentication – refers to the protection of multimedia content against unauthorized changes. By means of data hiding technologies the exact areas inside the multimedia content, which have been modified without authorization, can be detected and the changes can be even reversed [7].
The fifth application area – multimedia fingerprinting – also concerns the protection of intellectual property rights. In close similarity to the proof of ownership application, data hiding methods embed information about the buyer or the legitimate user of the multimedia content. In this way, if actions violating the rights of the copyright holder are undertaken – such as the illegal distribution of the multimedia content over the Internet – the perpetrator can be identified by means of the secret information embedded in the distributed copies.
The five data hiding application areas presented above enumerate only the most important and widespread web-relevant uses of data hiding. The World Wide Web is a highly dynamic field and the list may be easily expanded by new data hiding application areas with each major advance of modern information and communication technologies.
References:
[1] I. J. Cox, M. Miller, J. Bloom, J. Fridrich, and T. Kalker, Digital Watermarking and Steganography, 2nd ed.: Morgan Kaufmann Publishers, 2008.
[2] E. Cole, Hiding in Plain Sight: Steganography and the Art of Covert Communication, 1st ed.: John Wiley & Sons, 2003.
[3] S. Katzenbeisser and F. Petitcolas, Information Hiding Techniques for Steganography and Digital Watermarking, 1st ed.: Artech House, 2000.
[4] G. Kipper, Investigator's Guide to Steganography, 1st ed.: Auerbach Publications, 2004.
[5] C. Lu, Multimedia Security: Steganography and Digital Watermarking Techniques for Protection of Intellectual Property, 1st ed.: Idea Group Publishing, 2005.
[6] R. J. Anderson, R. M. Needham, and A. Shamshir, "The Steganographic File System," in Second International Workshop on Information Hiding, vol. 1525 of Lecture Notes in Computer Science, Portland, 1998, pp. 73-82.
[7] J. Fridrich and M. Goljan, "Protection of Digital Images Using Self Embedding," in Symposium on Content Security and Data Hiding in Digital Media, New Jersey Institute of Technology, 1999.
