A major design goal of the World Wide Web is to provide universally available means for human communication, commerce, and opportunities to share knowledge [1]. The number of its users amounted to almost 1.6 Milliard in 2008 [2], which emphasizes its significance as an information sharing medium. Tim O’Reilly ([3], p. 2, [4] and [5]) summarizes that: "Network effects from user contributions are the key to market dominance in the Web 2.0 era". The creation of such global network effects depends heavily on a free flow of information and a free access to knowledge.
Despite this important trend towards freedom in information distribution, security approaches enabling private communication ([6], [7]) or the protection of intellectual property ([8], [9], [10]) are still needed. Traditional cryptographic approaches like communication channel encryption or DRM technologies, which are a widespread method of choice for protecting intellectual property, offer one solution, but they have a number of weak points. They either:
- Encrypt the whole digital content, which has two major disadvantages: it fully restricts the free flow of information and it announces the existence of the encrypted content to potential attackers, or
- Attach an encrypted "signature" to the multimedia host, which has one major disadvantage: the signature is not native to the multimedia host and can be easily detected, lost or deliberately removed.
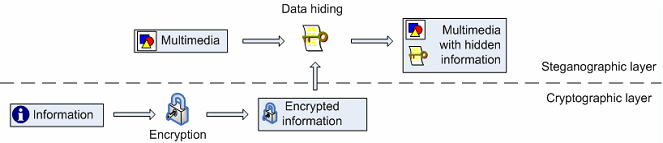
Fig. 1: Data hiding of encrypted information
Data hiding can enhance existing cryptographic solutions ([11], [12], [13] and [14]) and alleviate the aforementioned disadvantages by hiding the encrypted data into the multimedia content (Fig. 1). In this way data hiding preserves the freedom of easy access to multimedia content and provides difficult-to-detect and difficult-to-remove mechanisms capable of transmitting secret messages, storing private information or keeping track of content authors, digital copies and rightful owners.
Data hiding web services can be provided or used in addition to and on top of any cryptographic web services already in use by a company. The input for these services is the multimedia host itself, the chosen data hiding algorithm and the secret encrypted data (in case of encoding). The output is a multimedia host containing hidden data. As data hiding services act on and produce multimedia content, their integration into an existing infrastructure which already works with multimedia should not be very difficult. In addition, they (unlike cryptography) ensure backwards compatibility with systems which do not consider security issues.
References:
[1] World Wide Web Consortium. About W3C: Goals. URL: http://www.w3.org/Consortium/mission (accessed May 9, 2009).
[2] Miniwatts Marketing Group. Internet Usage Statistics. URL: http://www.internetworldstats.com/stats.htm (accessed May 9, 2009).
[3] T. O'Reilly. (2005) What is Web 2.0. URL: http://www.oreillynet.com/pub/a/oreilly/tim/news/2005/09/30/what-is-web-... (accessed May 9, 2009).
[4] T. O'Reilly. (2006) Web 2.0 Compact Definition: Trying Again. URL: http://radar.oreilly.com/2006/12/web-20-compact-definition-tryi.html (accessed May 9, 2009).
[5] T. O'Reilly. (2006) Harnessing Collective Intelligence. [Online]. URL: http://radar.oreilly.com/2006/11/harnessing-collective-intellig.html (accessed May 9, 2009).
[6] Y. Peng and Q. Wu, "Secure Communication and Access Control for Web Services Container," in Fifth International Conference on Grid and Cooperative Computing (GCC), 2006, pp. 412-415.
[7] S. Zarandioon and Y., Ganapathy, V. Danfeng, "OMOS: A Framework for Secure Communication in Mashup Applications," in Computer Security Applications Conference, 2008, pp. 355-364.
[8] M. Farley, "Web 2.0, wikis, and the IP Community," Journal of Intellectual Property Law & Practice, vol. 2, no. 4, 2007.
[9] R. Gil, R. Tous, and J. Delgado, "Managing intellectual property rights in the WWW: patterns and semantics," in First International Conference on Automated Production of Cross Media Content for Multi-Channel Distribution, 2005.
[10] J. Garofalakis, P. Kappos, S. Sirmakessis, and G. Tzimas, "Digital Data Processing For Intellectual Property Rights Preservation Over World Wide Web," in 13th International Conference on Digital Signal Processing Proceedings, vol. 2, 1997, pp. 833-836.
[11] M. Backes and C. Cachin, "Public-key steganography with active attacks," in 2nd Theory of Cryptography Conference (TCC), vol. 3378 of Lecture Notes in Computer Science, 2005, pp. 210-226.
[12] R. J. Anderson and F. Petitcolas, "On the limits of steganography," IEEE Journal on Selected Areas in Communications, vol. 16, no. 4, pp. 474-481, 1998.
[13] A. Westfeld, "Steganalysis in the Presence of Weak Cryptography and Encoding," in Digital Watermarking. 5th International Workshop (IWDW), vol. LNCS 4283, Jeju Island, Korea, 2006, pp. 19-34.
[14] M. Peinado, F. Petitcolas, and D. Kirovski, "Digital rights management for digital cinema," Multimedia Systems, vol. 9, no. 3, September 2003.
